We simulate real attackers to identify exploitable weaknesses across your environment. You get evidence, impact, and a clear plan to fix the highest-risk items first
An attacker needs only one entry point to escalate and access critical assets.
Offensive testing replaces assumptions with evidence.
You learn exactly how an attacker could breach your environment, what they would target, and which controls fail.
That clarity shortens decision cycles for remediation and reduces the chance of an expensive breach.
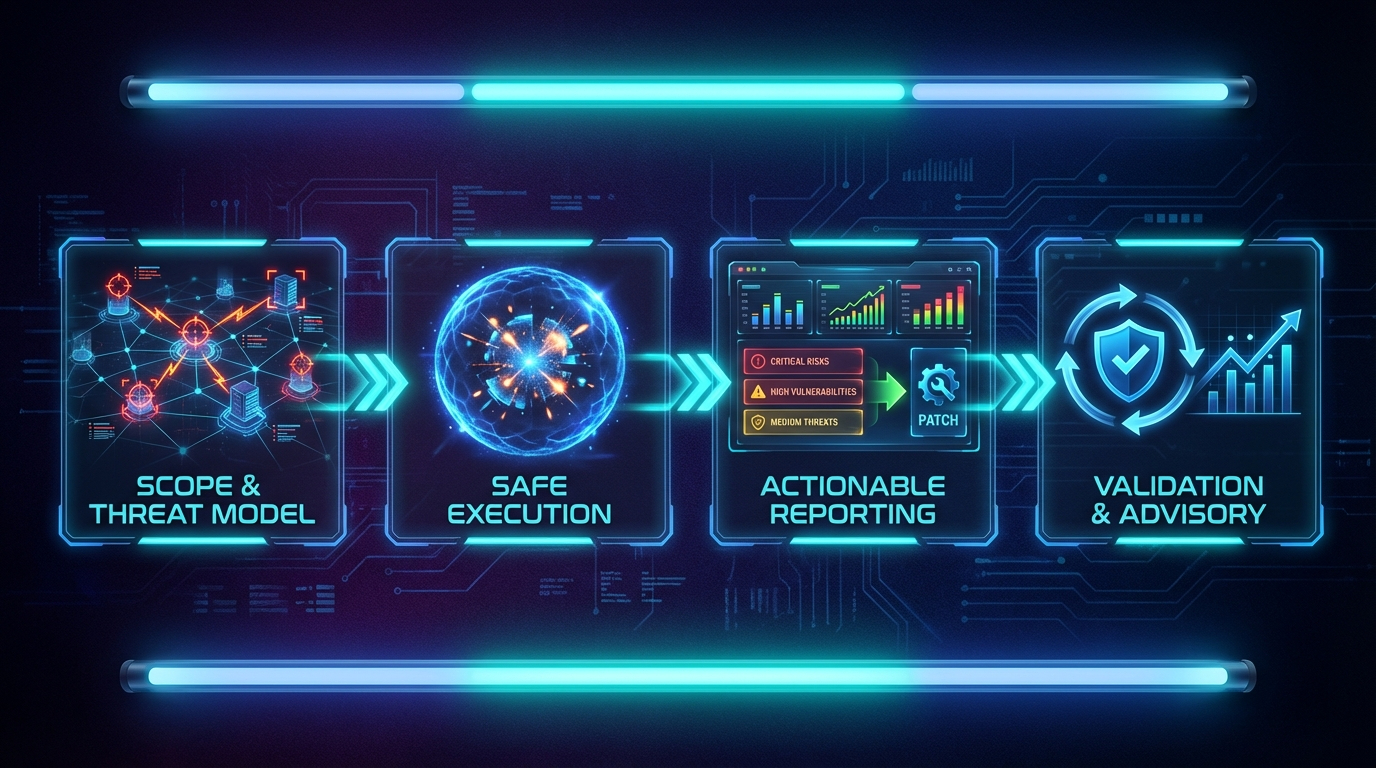
Actionable Reporting — every finding has PoC, affected assets, and risk rating to guide fixes

One-page risk view for leadership

Reproducible PoC, logs, screenshots, and exploit note

Ranked fixes, suggested owners, and effort estimates

Post-remediation test results and recommended detection rules
Request a scoping call to define scope, timeline, and constraints