We secure applications and sensitive data across cloud and on-prem environments to reduce breach impact
Applications and data are prime targets for attackers. Weak code, poor access controls, or misconfigured data stores can expose critical information.
Securing these layers reduces both breach likelihood and impact.
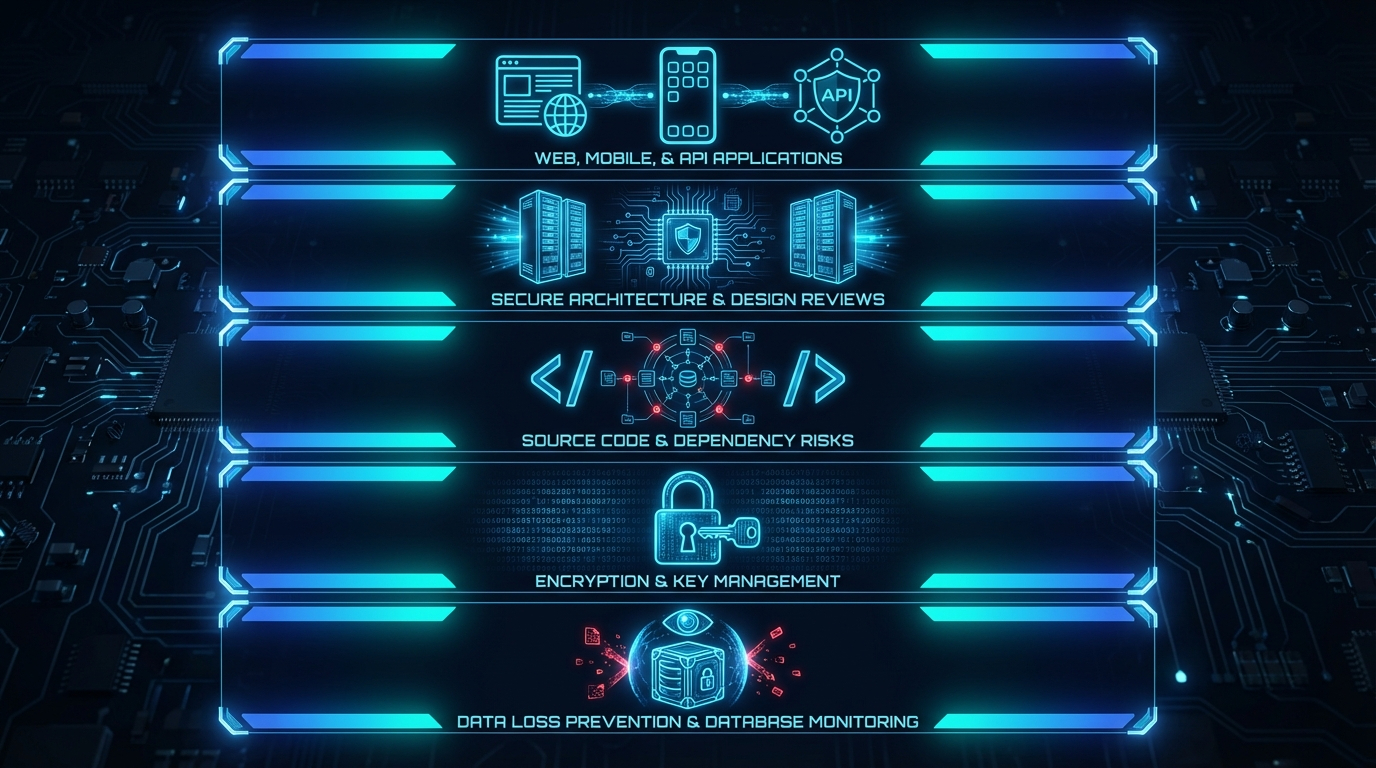

Application risk assessment with business impact

Code and configuration findings with remediation steps

Prioritized remediation guidance and owners

Validation testing results and advisory
Request an application security assessment